Imagine you’re having issues with a third-party service that is called whenever a user logs in. Occasionally, the service is unexpectedly unavailable, leaving users stranded when they wanted to sign in to make a purchase. This happens about once a month, resulting in frustrated customers and some scrambling by the dev team before finding the issue.
Making calls to a third-party application is outside the realm of CloudWatch’s abilities, but there is a way to leverage AWS to combat this issue by taking advantage of the cloud’s monitoring capabilities. In this article, Senior Developer Zachary Sersland walks you through an AWS .Net Lambda function example that will prevent your third-party authentication service from becoming unavailable.
Writing the Function in .Net
My first step was to create a new project in Visual Studio 2017. Create a new project, and under Installed -> AWS Lambda I selected AWS Lambda Project. I then created a class, LoginCheck (you can call the class and main function whatever you like), that would make a call to an existing service in my application that would call the third-party service and return a response code.
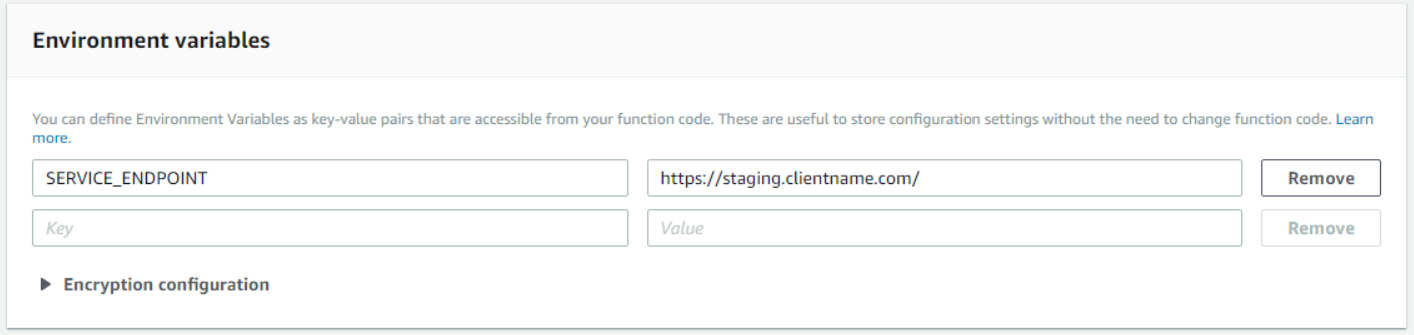
The following code declares a variable, ServiceEndpoint, that holds an environmental variable that I’ll declare in the Lambda function. The constructor sets ServiceEndpoint, while also logging a few helpful messages to let me know the function initiated correctly.
public string ServiceEndpoint { get; set; }
public LoginCheck()
{
LambdaLogger.Log("Lambda Test Begin");
ServiceEndpoint = Environment.GetEnvironmentVariable("SERVICE_ENDPOINT");
LambdaLogger.Log("Lambda End Constructor");
}Next, I write the function itself. This function builds the request URL and the content of the request. You then call the service and check the status of the response. If the request wasn’t successful, log the error and throw an exception that will be detected by CloudWatch.
public async Task FunctionHandler(ILambdaContext context)
{
LambdaLogger.Log("Lambda Test Sign In Event");
var requestURL = ServiceEndpoint + "/ajax/AWSServices.asmx/TestUserLogin";
var client = new HttpClient();
var content = new StringContent(string.Empty, Encoding.UTF8, "application/json");
var response = await client.PostAsync(requestURL, content);
if(response.IsSuccessStatusCode)
{
LambdaLogger.Log("Sign in request was successful.");
}
else
{
LambdaLogger.Log(await response.Content.ReadAsStringAsync());
throw new Exception(response.ToString());
}
}For more information on writing a function for lambda in Visual Studio, check out the AWS documentation.
Creating the Lambda Function
Next, I created the lambda function through the AWS console. Navigate to the Lambda page under Services -> Compute and click Create Function. Under Runtime, select C# (.Net Core 2.0) and under Role choose a role that has access to the necessary AWS services – in this case CloudWatch. Once the function is created, zip up your .Net project and upload it. Under Handler, specify the function that Lambda should call. The format of the handler test is “assembly::namespace.class-name::method-name”. In the case of my function, the handler was “ClientName.LoginCheck::ClientName.LoginCheck.LoginCheck::FunctionHandler”.
The environmental variables make it easy to specify variables without redeploying your entire function. In the case of this function, I made the service endpoint an environmental variable to make it easier to test in our staging environment. When the function was tested in staging, deploying to production was as easy as changing the variable.
Scheduling
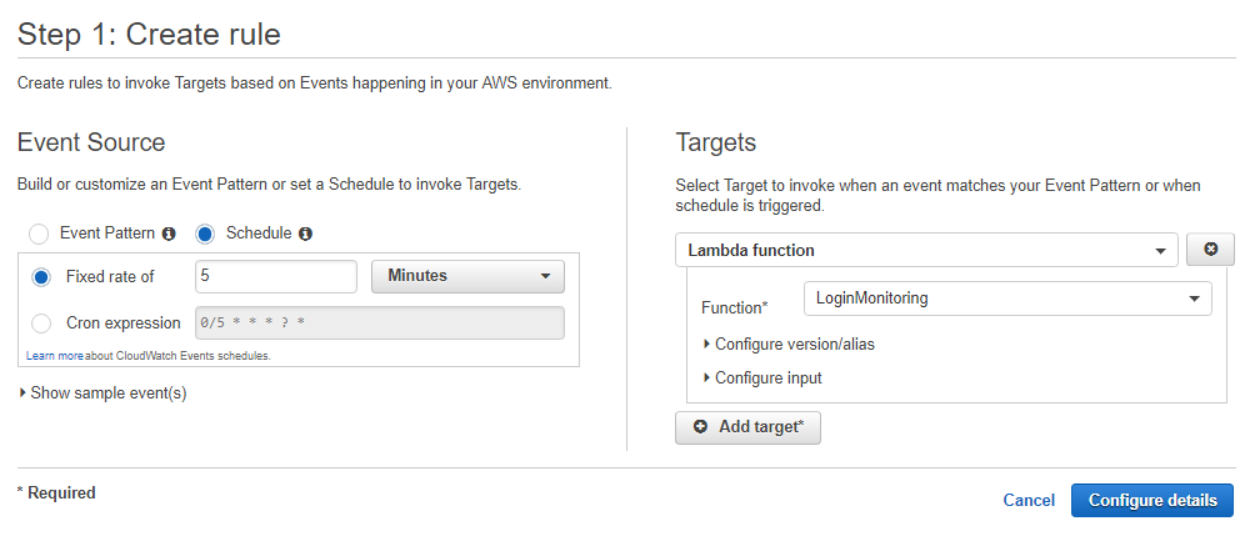
The next step is to schedule the lambda function to run every five minutes. To do this, access CloudWatch -> Events -> Rules and click Create Rule. Under Event Source select Schedule -> Fixed Rate. For this function I chose 5 minutes, but you can select any interval and, if you want to get fancy, implement a cron expression. Under Targeting, select Lambda Function and find the name of your function.
Now that our job is running every five minutes, we’ll monitor when it fails and notify stakeholders when it does.
Monitoring
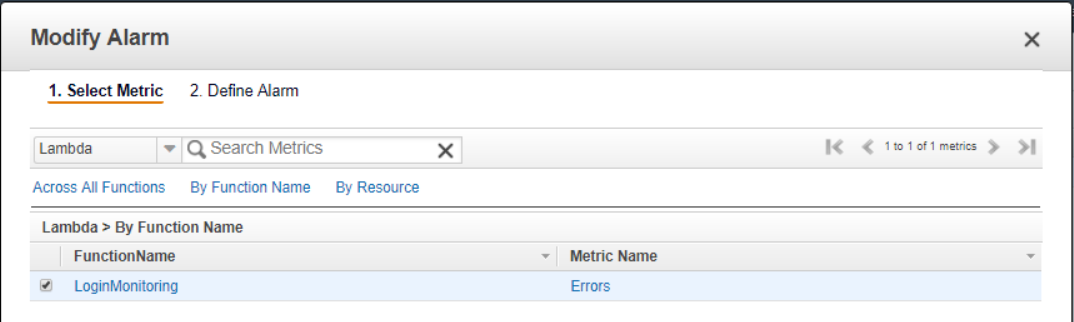
Stay in CloudWatch and navigate to the Events page. Select Lambda, pick out your function, and choose Errors for metric (this is why I threw an exception when the service call failed in the lambda function).
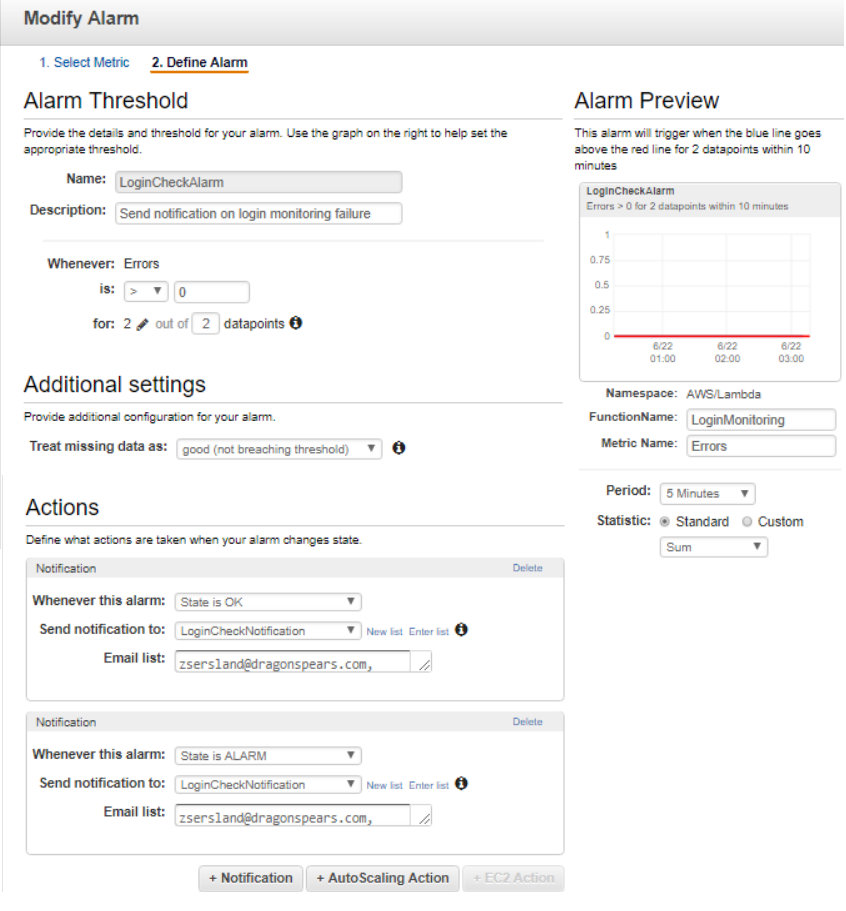
The next page is heavily customizable, and it depends greatly on the needs of the function what should be selected on this page. I used quite a bit of trial and error before settling on a configuration. I set the period to five minutes to match the Event interval, and under Alarm Threshold I selected two failing datapoints in a row. Under Actions, I specified who should be notified when the alarm fails and when it’s back to normal.
When all of this is set up, you can rest easy knowing that, if your inbox is empty, your services are running as expected. For more information about leveraging well known and lesser known AWS Services,  .
.